
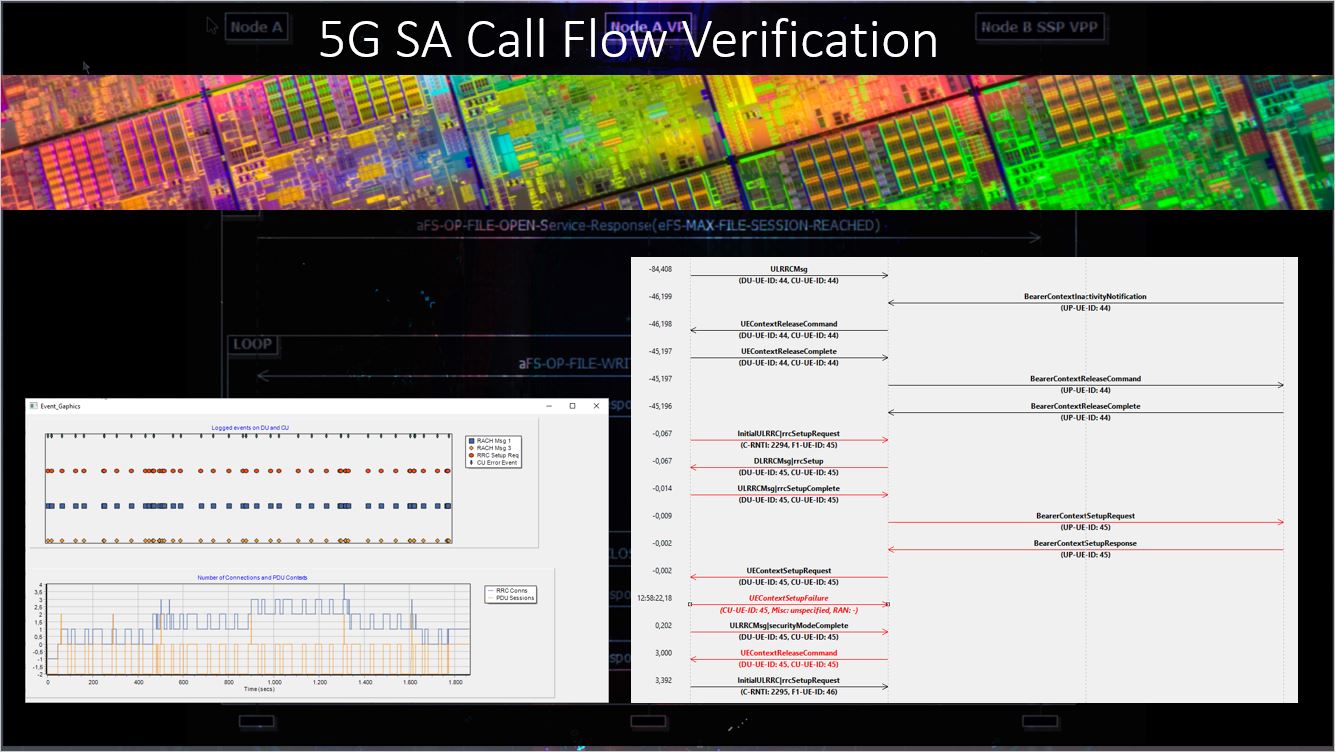
The verification is based on PCAP files captured on RAN interfaces e.g. F1-, E1- and NG-Itf. The Protocol Engine converts encoded byte streams to JSON format and includes 2nd stage decoding for imported protocol elements. Call Trace functionality identifies messages belonging to a certain call flow based on various identities, such as CRNTI, DU/CU/UP/AMF UE ID, TMSI, IMSI … Various triggers, assigned to a set of messages during protocol extensions, are fed into State Machines for CU interfaces. This allows to mark failed or suspicious calls and resent the result to the user in a customized representation.
Failure analysis is a cumbersome task due to high volume of data to be processed and different event sources to be correlated. A grahical representation is the most convenient way to present events and call flows. Various filters allow to narrow down the messages excahned to the interesting points.